The Cyber Kill Chain concept developed by Lockheed Martin provides the basis of the intelligence-driven defense. Do note that the attackers have the liberty of time on their side. They may be working on planning an attack for as long as they desire. This is the pre-compromise stage starting with reconnaissance (due diligence) of the target.
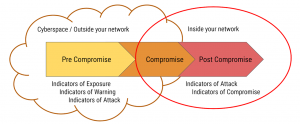
When attackers are performing reconnaissance, your organization is more probable to be targeted if it has a weak security posture visible from cyberspace. Reconnaissance of a ‘digital footprint’ includes a survey of your cyber inventory with details on your publicly available information such as domains, hosts, digital certificates, social media accounts, etc. Auditing this information against a secure practice will determine how secure you appear from a hacker’s perspective. These gaps give you data points in the form of ‘Indicators of Exposure’.
If and when an attacker does select your organization as the target, they start building the attack pieces. They may register a lookalike domain, a bogus digital certificate, impersonated social media account, or even an executive profile, all these are some of the many ‘Indicators of Warning’ that organizations should take action against.
‘Indicators of Attack’ are the signs (data points) that reflect an ongoing attack specifically targeting your organization. A phishing page, impersonated Email, a malvertising document, your IP or Host in a blacklist are just some of the many data points that reflect a financial scam, malware injection, data exfiltration attack and more.
The big question: Is your current practice of managing attacks within networks (IOCs) sufficient or must it be augmented by an offensive defense approach? Detecting and mitigating at an early stage greatly reduces cyber risk as it tackles data points (IoE, IoW, IoA) in the attacker’s territory. It also means organisations can improve defenses by dismantling an attack in the pre-compromise stage.
The offensive defense approach is challenging because of the evolving nature of cyberattacks where new variations of attack categories need to be continuously identified. Indicators of Exposure, Warning, and Attacks are a moving target requiring innovative and dynamic systems, augmented by qualified threat analysts to effectively detect and mitigate. If done appropriately, the ROI is exponentially high.










Discussion about this post