Analysis by the Security Response Team (SRT) at Tenable has determined that over 102 million healthcare records were exposed in 2020 as a result of data breaches. Almost three million health records have already been exposed in the first two months of 2021. The threat to healthcare should come as no surprise, given the growing demand for telehealth appointments, medical supplies and a race for vaccine development and distribution.
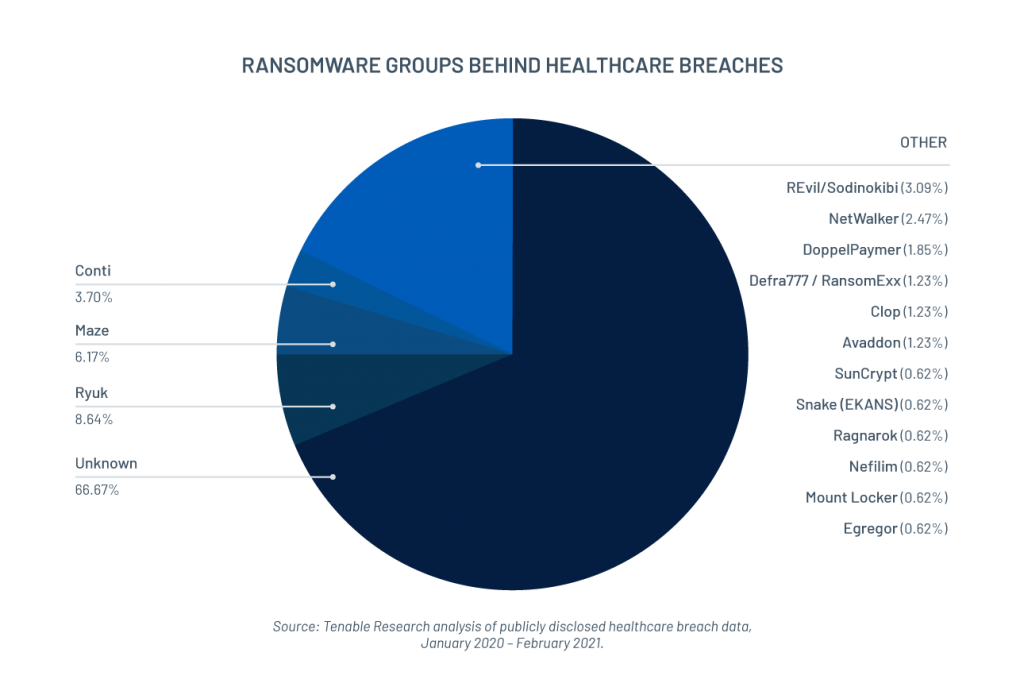 When looking at the root cause of these attacks, ransomware was by far the most prominent, accounting for a whopping 54.95% of breaches. Ryuk stood out above the rest, repeatedly appearing in breach disclosures and accounting for 8.64% of ransomware-related breaches, followed by Maze (6.17%), Conti (3.7%) and REvil/Sodinokibi (3.09%).
When looking at the root cause of these attacks, ransomware was by far the most prominent, accounting for a whopping 54.95% of breaches. Ryuk stood out above the rest, repeatedly appearing in breach disclosures and accounting for 8.64% of ransomware-related breaches, followed by Maze (6.17%), Conti (3.7%) and REvil/Sodinokibi (3.09%).
SRTs analysis revealed that third-party breaches accounted for over a quarter of the breaches tracked and nearly 12 million exposed records. Other leading causes of data breaches included email compromise/phishing (21.16%), insider threat (7.17%) and unsecured databases (3.75%).
“As the ongoing COVID-19 pandemic continues to place unprecedented strain on global healthcare infrastructure, attackers are finding what was already an attractive target even more enticing,” explained Rody Quinlan, Security Response Manager, Tenable. “These attacks are not going away anytime soon so it’s imperative organisations, particularly those being targeted in the healthcare sector, understand the threats against them and have the resources necessary to reduce their cyber risk.”
Ryuk ransomware, the leading culprit for ransomware attacks against the healthcare industry, is known to favor a number of vulnerabilities including Zerologon, one of the most prominent vulnerabilities of 2020.
In order to reduce the risk of compromise, healthcare organisations should:
- Prioritise vulnerabilities: identify and remediate the most business-impacting vulnerabilities.
- Address the root cause: once the vulnerabilities most likely to introduce business risk are identified and prioritised, remediate them and continue regular maintenance check-ups.










Discussion about this post