
Schools and universities, with their treasure troves of sensitive data and often insufficient cyber security measures, have become prime targets for cybercriminals. This is evident in the latest report from Check Point Research, the Threat Intelligence arm of Check Point Software Technologies which found that the Education sector has been the most targeted industry for cyberattacks so far in 2024. The data also shows a disparity when comparing sectors and regional differences.
Education in focus
From the beginning of the year to the end of July, the Education/Research sector has been the most targeted industry globally, with an average of 3,086 attacks per organisation, per week. That is a 37% increase compared to the previous year, as opposed to the next most targeted industry, Utilities.
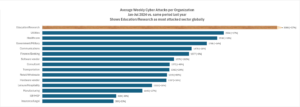
Figure 1. Average weekly attacks per organisation in 2024 vs 2023
Overall attacks per region
The APAC region has seen the most cyberattacks against organisations in the Education/Research sector since the beginning of the year, with 6,002 weekly attacks per organisation. However, North America experienced the highest YoY increase with a 127% rise.
| Region | Average of Attacks per Organisation | Change YoY |
| APAC | 6002 | -37% |
| Africa | 2875 | +70% |
| Europe | 2804 | +18% |
| Latin America | 2721 | +88% |
| North America | 1821 | +127% |
Overall attacks per country
India is the most targeted country in the Education/Research sector, with 6,874 weekly attacks per organisation, representing a 97% YoY increase. Other notable changes include Germany (^66%) and Portugal (^66%).
India seems to experience the most attacks mainly due to the rapid adoption of remote learning fueled by the COVID lockdowns and the ongoing digitisation of education, which have created lucrative opportunities for cybercriminals seeking to steal personally identifiable information (PII) to sell on the Dark Web. Additionally, the proliferation of these online learning platforms catering to everyone from preschoolers to retired professionals has increased cyber risks as schools and universities often do not emphasize cyber security sufficiently, leaving their networks vulnerable. The diverse groups involved in these educational networks—including students, teachers, parents, and educational professionals—further expand the attack surface, providing multiple weak points for malware insertion and unauthorised access to financial and PII data.
| Country | Average of Attacks per Organisation | Change YoY |
| India | 6874 | +97% |
| United Kingdom | 4793 | +36% |
| Italy | 4730 | +40% |
| Mexico | 3507 | +22% |
| Portugal | 3042 | +66% |
| Germany | 2041 | +77% |
| United States | 1667 | +38% |
Why are schools targeted by cybercriminals?
Part of the appeal is the sheer number of personal details retained by education institutions. In most companies you tend to only have employees whereas schools, colleges and universities don’t just have employees like teachers and lecturers, they also have students. With so many more people, this makes networks in the sector much bigger, more open and more difficult to protect. Plus, that also means there is so much personally identifiable information (PII) that can be used for financial gain.
Students are not employees beholden to strict corporate guidelines on appropriate access to networks. They bring their own devices on campus, work from shared student accommodation, and connect to free public Wi-Fi without thinking about the security risks first and foremost. This combination has contributed to the perfect storm.
Files Phishing Campaign
Ahead of the upcoming school year, Check Point observed 12,234 new domains created related to schools and education, marking a 9% increase YoY. Among these, 1 in every 45 domains were found to be malicious or suspicious.
In July 2024, Check Point Research observed multiple phishing campaigns in the USA that use file names related to school activities to lure victims. The first campaign, associated with the file name “DEBIT NOTE_ {name and date} _schoolspecialty.com.html” (figure 2) and emulated an Adobe PDF sign-in message.
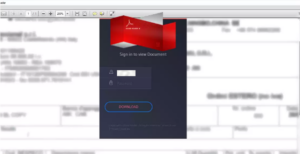
Figure 2: the file “DEBIT NOTE {name and date} _schoolspecialty.com.html”
Another campaign used the file name “{school name} High School July Open Enrollment for Health & Financial Benefits.htm”(figure 3) and contained highly obfuscated code, appearing to display a Microsoft login page for some organisation.
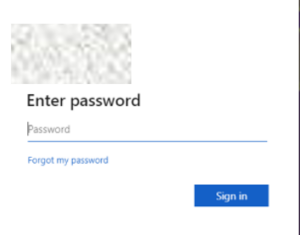
Figure 3: “{school name} High School July Open Enrollment for Health & Financial Benefits.html”
Ram Narayanan, Country Manager at Check Point Software Technologies, Middle East, said, “With the education sector experiencing an unprecedented volume of attacks so far this year, it is evident that schools, colleges and universities are at the forefront of cybercriminals’ agenda. This surge illustrates the critical need for robust cybersecurity measures and heightened awareness within educational institutions to safeguard sensitive data and maintain operational integrity.”










Discussion about this post